Formidable eSign: A Healthcare-Grade Digital Signing Framework for Structured Clinical Data
This whitepaper presents the architecture of the Formidable eSign framework—a digital signing system purpose-built for the rigorous demands of healthcare. It offers a deep dive for technical experts, security professionals, and regulatory leaders seeking robust methods to guarantee the long-term integrity and authenticity of clinical data across distributed environments.
Table of Contents
Access Full Document
Enter your email address to continue reading this technical whitepaper.
Introduction: Securing Clinical Data in a Distributed Ecosystem
In modern healthcare, clinical information is increasingly exchanged as structured data, such as FHIR or JSON, between independent systems like hospitals, pharmacies, and regulatory bodies. In this distributed ecosystem, guaranteeing the integrity of the clinical content—proving that it has not been altered since it was signed—is as critical as verifying the identity of the signer.
The core problem this document addresses is the failure of traditional digital signing models to provide durable, cryptographic proof of content integrity for structured data over the long term. Many conventional systems can prove who signed a transaction but cannot cryptographically prove what exactly was signed, leaving a critical security gap in workflows for prescriptions, medical orders, and regulatory submissions. Formidable eSign is a framework engineered specifically to solve this challenge by creating an unbreakable link between the signer's identity and the precise clinical data they approved. To understand this solution, one must first appreciate the fundamental gap in conventional signing approaches.
The Fundamental Challenge: The Identity-Integrity Gap in Healthcare
Distinguishing between signer identity and content integrity is the central security challenge in modern digital healthcare workflows. While related, they are not the same, and assuming one implies the other is a dangerous oversimplification. A signature platform must provide formal, independent guarantees for both.
"Who Signed?" vs. "What Exactly Was Signed?"
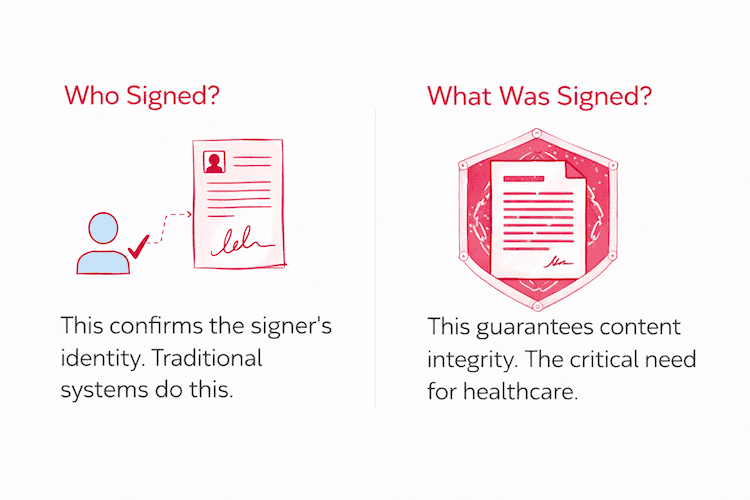
Traditional digital signing has long provided a robust answer to the first question: "Who signed?" Through the established mechanisms of Public Key Infrastructure (PKI), a digital signature can cryptographically prove the identity of the keyholder who authorized a transaction. However, healthcare systems require an equally definitive and cryptographic answer to the second, more nuanced question: "What exactly was signed?" A digital signature is not a snapshot of a document; it is a mathematical proof that a specific key signed a specific input. If that input is not explicitly and deterministically derived from the clinical content, then the integrity of that content cannot be proven later.
Why Structured Data Breaks Naïve Signing Models
The properties of structured data formats like FHIR and JSON make them inherently incompatible with simple signing approaches that treat the data as an opaque blob. Two documents that are semantically and clinically identical can be cryptographically different, rendering naïve signature validation unreliable and unsafe. Key properties include:
- Mutability and transformations: Gateways, intermediaries, and ETL processes frequently enrich, strip, or transform data as it moves between systems.
- Insignificant variations: The order of keys in a JSON object or the amount of whitespace used in serialization is not semantically significant but will produce a completely different byte stream.
- Normalization and regeneration: Data is often stored in databases and regenerated into JSON format on demand, a process that may not reproduce the original byte-for-byte representation.
The consequence is a catastrophic failure of the integrity guarantee: a signature over raw JSON is rendered cryptographically meaningless by routine system operations, making it impossible to distinguish between benign transformations and malicious tampering. The Formidable eSign framework's design is directly informed by a rigorous analysis of these threats.
Security Model and Threat Analysis
Formidable eSign is designed for a high-assurance operational environment where signed artifacts must remain verifiable across untrusted networks and independent systems, potentially years after their creation. The threat model therefore assumes a zero-trust approach to data integrity, where intermediaries are not trusted to preserve data and vendor-controlled infrastructure cannot be a dependency for verification.
The table below outlines the threats the framework is designed to mitigate, as well as those that are explicitly handled by other security controls within the broader ecosystem.
| Threats Addressed | Threats Explicitly Out of Scope |
|---|---|
| Post-signature data modification (intentional or accidental) | Compromise of signer private key (handled via PKI revocation) |
| Data transformation by intermediaries (gateways, ETLs, databases) | Malicious but authorized signing |
| Replay of valid signatures with altered payloads | Endpoint compromise on clinician devices |
| Loss of signing-server state | |
| Long-term verification after system decommissioning |
The following sections detail the architectural solution designed to mitigate these in-scope threats by embedding all integrity guarantees directly into the signed artifact itself.
The Formidable eSign Architecture: A Two-Pillar Approach to Integrity
To create an unforgeable and durable link between a signer and the approved clinical content, Formidable eSign's core design principle is to sign a deterministic fingerprint of the content, not the raw, unstable data itself. This is achieved through a mandatory, two-step process that forms the foundation of its security guarantees.
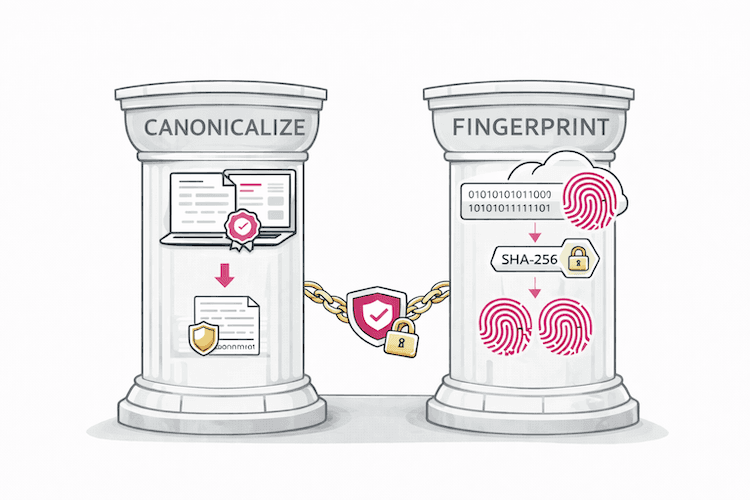
Pillar 1: Canonicalization (Deterministic Serialization)
Canonicalization is a mandatory pre-signing step that transforms a structured clinical document into a standard, unique byte stream. This process ensures that any two documents that are semantically identical will produce the exact same output for hashing, regardless of non-significant variations like field order or whitespace.
This step is critical for JSON-based data, which is inherently unordered and insensitive to whitespace. Without it, cryptographic hashes are unstable and signature validation becomes non-repeatable. The Formidable eSign approach utilizes a documented and versioned canonicalization profile that normalizes object key ordering, numeric and string representations, and character encoding. Crucially, the version number of the canonicalization profile used is included as signed metadata. This guarantees that the hashing process is reproducible and verifiable across different systems and over long periods, ensuring forward compatibility and long-term auditability.
Pillar 2: Fingerprinting (Cryptographic Hashing)
The fingerprint is a cryptographically secure hash (e.g., SHA-256) of the canonicalized document produced in the first step. This fingerprint serves as a compact and unique proxy for the entire clinical document. Its essential properties are:
- It uniquely represents the full content of the document.
- It is collision-resistant, meaning it is computationally infeasible to find two different documents that produce the same hash.
- It is deterministic, meaning the same canonicalized input will always produce the same fingerprint.
The security implication of this approach is absolute: any change to the underlying clinical data—an altered medication name, a modified dosage, a different patient identifier—will result in a completely different fingerprint. This mismatch causes signature verification to fail immediately and unambiguously, providing a clear signal of tampering. This provides a binary, fail-closed guarantee: the signature is either valid for the exact original content, or it is invalid. There is no ambiguity. These two pillars are systematically implemented in the framework's signing and validation workflows.
Cryptographic Workflows and Artifacts
The security of the Formidable eSign framework relies on well-defined, independent signing and validation workflows. This sequence of operations produces a self-contained, portable proof of integrity that does not depend on the availability of the original signing server or any proprietary databases.
The Signing Flow
The signing operation is a precise sequence of steps designed to protect both the integrity of the data and the security of the signer's private key.
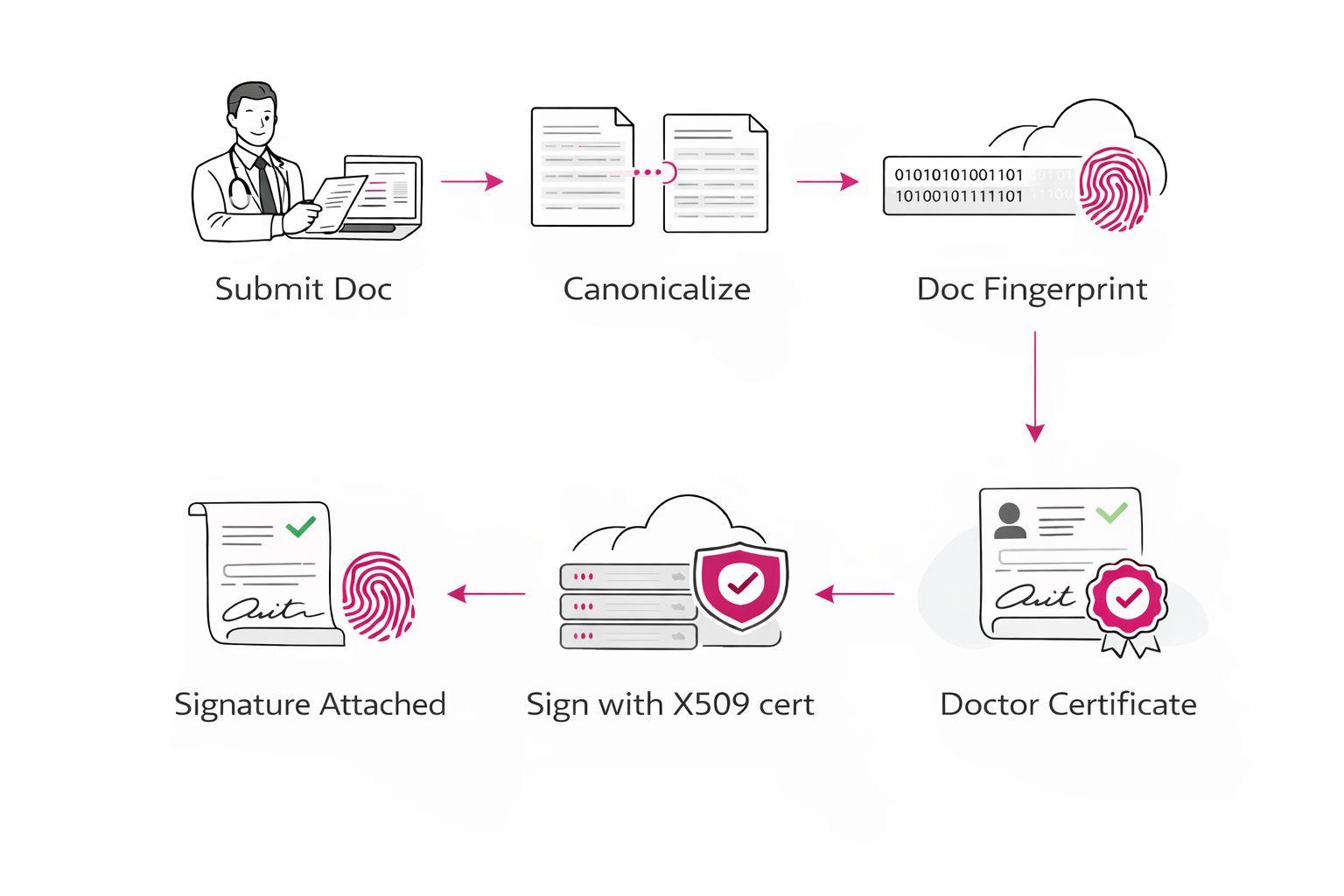
- A healthcare professional submits the structured clinical document (e.g., a FHIR prescription) for signing.
- The document is processed through the specific, versioned canonicalization profile to produce a deterministic byte stream.
- A cryptographic fingerprint (hash) is computed from the canonicalized data.
- Only the fingerprint and an identifier for the signer's certificate are sent to the signing service. Crucially, the sensitive clinical document never leaves the trusted client environment, ensuring the signing service remains a zero-knowledge component in the workflow.
- The signing service uses the certificate identifier to retrieve the corresponding private key, which is protected within aHardware Security Module (HSM).
- A digital signature is generated over the fingerprint. The resulting signature artifact is returned to be attached to or stored alongside the original document.
The final signature artifact is a self-contained package containing all the data necessary for independent verification:
- The digital signature value.
- The hash that was signed.
- An identifier for the hash algorithm used (e.g., SHA-256).
- The version of the canonicalization profile used.
- A reference to the public certificate of the signer.
The Independent Validation Flow
The validation process allows any third party to verify the document's integrity without contacting the original signing service.
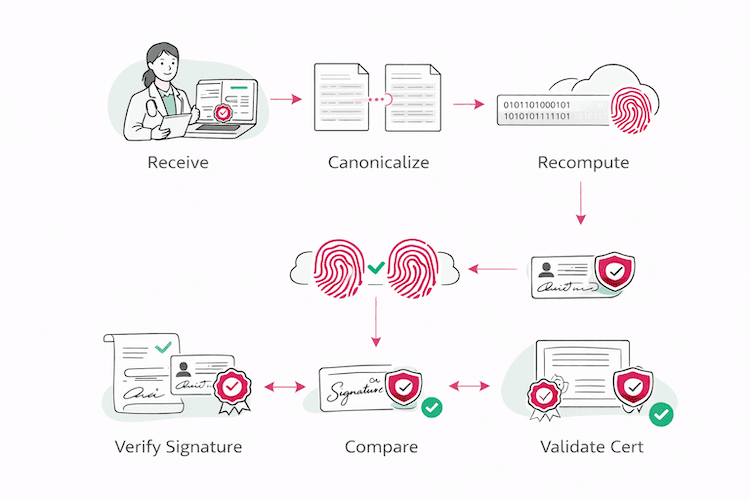
- The verifier receives the document and its associated signature artifact.
- Using the canonicalization version specified in the signature metadata, the verifier re-canonicalizes the received document.
- The verifier re-computes the hash of the canonicalized document.
- This newly computed hash is compared to the signed hash contained in the signature artifact.
- The verifier uses the signer's public key (from the referenced certificate) to cryptographically verify the signature itself.
- The verifier validates the entire certificate chain up to a trusted root authority and checks for certificate revocation.
Validation is explicitly "fail-closed." A mismatch at any step—a different hash, an invalid signature, an expired certificate—results in the unambiguous rejection of the document. The key benefit of this design is that it enables true independent verification with no reliance on the original signing server, vendor logs, or proprietary databases. This is the critical design principle of a self-contained security artifact: the cryptographic proof of integrity is inseparable from the data it protects. It travels with the document, ensuring that verification is a deterministic, mathematical process, not a procedural one dependent on external systems. The cryptographic proof is embedded in the data itself, supported by the underlying PKI trust infrastructure that anchors signer identity.
Public Key Infrastructure (PKI) Trust Model
While the framework's core innovation lies in guaranteeing content integrity, it relies on the established and robust trust services of Public Key Infrastructure (PKI) to manage and verify signer identity. Formidable eSign does not reinvent identity management; it integrates with standard PKI models to provide a complete solution.
Key aspects of the PKI trust model include:
- Certificate Usage: Signer identity is represented by standard X.509 digital certificates. The associated private keys are non-exportable and protected by HSM-backed infrastructure to prevent compromise. The public keys are distributed within the certificates for independent verification by any party.
- Trust Anchors: The model is flexible and supports various trust anchors to accommodate different regulatory and enterprise environments. This includes internal healthcare Certificate Authorities (CAs), intermediate CAs chained to a public CA (e.g., DigiCert), or pinned trust lists managed by a regulator.
- Separation of Concerns: The framework makes a clear and intentional distinction between roles. The choice of Certificate Authority (e.g., DigiCert) provides the trust anchor for signer identity. The Formidable eSign canonicalization and fingerprinting process provides the cryptographic guarantee of content integrity. The choice of CA does not affect the integrity guarantees.
This clear separation of concerns for identity and integrity starkly contrasts with traditional approaches, where the lines are often dangerously blurred.
Comparative Analysis: Formidable eSign vs. Traditional Signing Solutions
Understanding the specific architectural choices of Formidable eSign is best achieved by contrasting them with common industry practices, which are often ill-suited for the unique challenges of structured clinical data. Many traditional solutions work well for static files like PDFs but fail to provide cryptographic integrity guarantees in a distributed healthcare ecosystem.
The following table evaluates the Formidable eSign approach against these traditional solutions across several key dimensions.
| Dimension | Traditional Solutions | Formidable eSign |
|---|---|---|
| Data Type | Files / envelopes | Structured JSON / FHIR |
| Canonicalization | Often implicit or absent | Explicit, versioned |
| What is Signed | Request / blob | Content fingerprint |
| Integrity Guarantee | Procedural | Cryptographic |
| Server Dependency | High | None |
| Long-term Verification | Limited | Full |
| Audit Defensibility | Weak | Strong |
The core differentiator is clear: Formidable eSign elevates content integrity from an implementation detail, often addressed through procedural controls, to a first-class, cryptographic security property embedded directly within the signed data.
Conclusion: Formal Security Guarantees
In regulated healthcare environments, where patient safety and legal defensibility are paramount, digital signatures must provide non-negotiable, cryptographic proof of both signer identity and content integrity. Traditional signing models, built for static documents or tightly-coupled systems, fail to meet this standard when applied to the dynamic, distributed world of structured clinical data. The Formidable eSign framework addresses this gap by design.
By combining deterministic canonicalization, cryptographic fingerprinting, and standard PKI, the framework delivers a set of formal security guarantees essential for modern healthcare.
- Authenticity: Guarantees the signer's identity is cryptographically bound to the signature via PKI and can be traced to a trusted root authority.
- Integrity: Guarantees the clinical content has not been altered in any way since the time of signing.
- Non-repudiation: The signer cannot credibly deny having approved the exact content represented by the cryptographic fingerprint.
- Tamper-Evidence: Ensures that any post-signing modification to the clinical content is immediately and computationally detectable during verification.
- Independent Verifiability: Enables any third party to verify the signature and integrity without reliance on the original signing server, vendor logs, or any proprietary infrastructure.
This approach, by design, provides the minimal, sufficient, and cryptographically sound foundation required for secure structured data exchange in modern healthcare.
Implement Cryptographic Integrity for Your Healthcare Workflows
Formidable eSign provides the enterprise-grade digital signing framework detailed in this whitepaper. Whether you're building prescription systems, medical order workflows, or regulatory submission platforms, our solution delivers the cryptographic guarantees your organization requires.
For technical questions about the security model or integration details, please contact our security team.